Secured Remote Workforce for just S$2/day**
Unified Security Gateway with VPN Firewall for SME

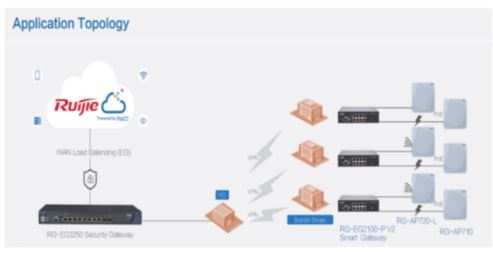
EasyGate (EG) Next-generation Unified Security Gateway is a multi-functional Cloud Managed Security Gateway product for various industries. Equipped with high- performance multi-core MIPS hardware architecture, the EG Gateway supports a wide range of features such as high-performance NAT, WAN load balancing, smart flow control, online behavior management, visualized IPsec VPN1, web authentication, etc .
EG Next-generation Unified Security Gateway is also supported by Central Cloud Management, altogether with switches and wireless access points, Cloud Management can provide a comprehensive secure networking platform for centralized management allowing for device monitoring, configuration as well as firmware management via web or mobile app.

Highlights
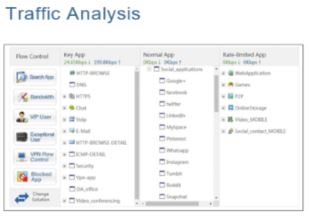
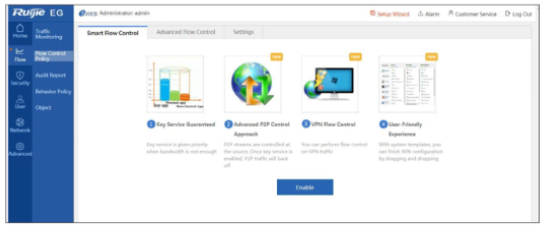
- Smart Flow Control & AAA Integration
- User Online Behavior Management
- VPN & Traffic Visualization
- Wireless Controller Functions
- FREE Cloud Management
- App Caching for Download Acceleration
- Built-in Power-Over-Ethernet
- Integration Mobile App Dummy Provisioning
Call us at:
+65-69500600 (SG) / +603-79800943 (MY)
WhatsApp: +65-92771818 (SG) / +6012-6478868 (MY)
** Per user/day costing with min 5 users & other conditions applied

 For this reason, we are recommending that organizations (for now) block port 445 from the internet, or further, use NGFW capabilities to block the SMB protocol itself from the internet.
For this reason, we are recommending that organizations (for now) block port 445 from the internet, or further, use NGFW capabilities to block the SMB protocol itself from the internet.











